Epistemic Status: I have worked for 1 year in a junior role at a large consulting company. Most security experts have much more knowledge regarding the culture and what matters in information security. My experiences are based on a sample size of five projects, each with different clients. It is therefore quite plausible that consulting in information security is very different from what I experienced. Feedback from a handful of other consultants supports my views.
I was very happy to learn that information security has recently been considered a promising career path for people who want to do good. I wondered whether information security would be a thing for me too. So I set out to look for jobs and ended up with one at a large consulting company pretty quickly.
It will likely never be easier to get jobs in information security than now. There is a so-called skills gap. The demand for security is going up swiftly as the importance of electronic information systems is ever increasing. Since training people takes time and scaling up training takes even more time, the current demand for security experts is far greater than the supply. Consultancies are lacking competent workforce quite badly. The CEO of the company that hired me said that "we have way more opportunities than we have people". Right now, some companies are inclined to hire any person that is capable of shouldering some workload and has some basic knowledge of IT-systems.
I thought, perfect! Maybe my search for a fulfilling career as a do-gooder is over. Not only do I get my hands on securing information systems for companies, nation-states and other groups, I also get to do consulting! Consulting has also been considered a promising path for various reasons.
Why I no longer think that consulting in information security is a good option
I was very interested in learning how my pre-existing theoretical knowledge compared to the practices in the company and how exactly projects would be like. To my surprise, I quickly found out that most projects are really poor. Few of my colleagues felt as strongly about this as I did, but most agreed. What do I mean by "really poor"?
Most projects have a flawed methodology that leads to no actual improvements in security
In fact, most projects had no methodology or theory of change at all. These projects would be like this:
Consultant: Do you have [some software] installed?
Client: Well, we have tinkered with it, but decided against it, it is just too expensive.
Consultant [writes a report]: There is no instance of [some software] installed. The solution is therefore highly insecure.
And that would be it. Other projects had a methodology that did not work. My personal favorite is the use of subjective scores, like 1 to 5, to grade the security of a solution. After a meeting with a client we would be like: "They do not have [a software that I happen to know] installed, that is no better than a 3, don't ya think?". We would then do all kinds of fancy arithmetic with those numbers, finally extinguishing all meaning that they originally had, to come up with a picture that we thought the client would like.
People often lack necessary skills to carry out the project
I guess that my colleagues by and large do not sense that what they are doing is not benefitting the security of the client. Information security experts are often great in a specific technical field, be it hands-on networking, programming or configuring machines. When it comes to research and study design however, my colleagues lacked important skills.
Furthermore, I noted very often that even basic terminology is not clear. Words such as remediation, vigilance, resilience and others are quite frequently used without a shared definition. Basic terms like security and risk, are often used wrong, indicating that the person does not really know what a risk is. In fact, I estimate that only around 1 consultant out of 10 has a probabilistic understanding of the concept risk. I still have no sufficient explanation for this.
Overall, there was a very heterogeneous people-landscape in the company. Some new-joiners had no IT-related experience. They then sat next to security-crackheads that have spent the last 25 years pentesting various systems.
Projects are just as good as they need to be
Most consultants are primarily motivated by 1) money and 2) social prestige. Both only weakly relate to security improvements. The goal of projects is not to secure the clients assets as well as possible, but rather to secure additional funding with as little effort as possible. Whilst that is obvious, it is astonishing how inefficient projects are.
The attentive reader might have asked himself by now: If the consultants do not produce high-quality work, lack skills and fail to secure the clients assets, why in the world would anyone in their right mind pay for such projects?
This is something that I am still very confused about. My leading theory: The clients are not in their right mind. The companies that have the weakest security posture and the greatest demand may purchase consultants in the hope that they will help them. But these companies are the ones that are incapable of overseeing the work of consultants. I am sure that there are tons of groups who have great security programs, but these are not the ones that would have hired us.
The culture in InfoSec consulting is harmful for effective security
There is a lot more to this than I can present here. I also do not know what parts of the culture come from the field of information security and which do come from consulting.
One thing stands out: It seems to be general practice to over-inflate your abilities and to come off as much more knowledgeable than you are. Colleagues of mine openly shared strategies for doing so.
Interlude (solely for purposes of entertainment):
How to come off as though you know what they are talking about but you don't
1. Ask questions using the others language
2. Sit through the awkward silence
Possible situation - Variables (A;B;C;D) mark terms and concepts that are unknown to the consultant:
Client: We did have trouble fixing B, due to A.
Consultant: Oh yeah, A is tough for other clients as well. How are you dealing with B now?
[awkward silence]
Client: Umm, I am not sure what you mean exactly.
[awkward silence]
Client: Do you mean how do we address C to enrich B with D?
Consultant: Yes.
Client: Ahh, well, we ... [potentially understandable information]
I did not learn a lot that I would consider valuable for solving pressing problems. Most of the skills that I acquired related to getting through the administrative overhead quicker. That is, I learned to half-ass fancy slides.
80000 Hours has stopped recommending general consulting as a viable career path to do as much good as possible. My impression is that they also think that the acquired skills are not very valuable for other areas.
Information security consulting is unlikely to improve your relevant skills as much as other options and there is a great chance that you have no impact.
The better alternative: self-study information security
Next to my job in consulting I also self-studied. I discovered that many of my colleagues had poor knowledge of topics and concepts that one stumbles over really quickly. Most employees in information security seem not to concern themselves with textbooks. Rather, they learn from others and from formal training. I think that self-study is going to get you into a position where you can have an impact much sooner. Note that this is rarely the only alternative, but one that many people have. Here are some recommendations and places to start.
Do
You need a quantitative understanding of security which you wont get from reading most of the literature. The book is a must-read.
- Properly build and secure your home network
This provides a way of getting hands-on experience with common network components.
- Do CTFs
You can do CTFs alone here or here or in many other places. Finding or founding a CTF-Team is great but difficult and not at all necessary.
Offensive experience gives you a better understanding of what kinds of systems are easy to hack and which are more secure. It allows you to take the perspective of an attacker and better estimate the security of a solution.
- Sign up to Bruce Schneier's newsletter Crypto-Gram
This newsletter covers a very broad range of topics. This will broaden your understanding of what kind of topics are part of information security and discover what you find interesting.
- Learn the basics of cryptography
Cryptography is the reason that secure communication is possible at all. Most security solutions rely to some degree on cryptographic concepts.
- Join the EA InfoSec facebook group
Do not
- Use buzzwords
- Pursue formal certificates
I have one and the test was so cheap that I am now ashamed of having done it. I have not told my superiors or anyone else that I passed and will not show it to anyone else. Also, the "learning materials" vary in quality. You will learn quicker on your own.
- Learn about industry norms
Norms are often a good source of inspiration, but usually poorly written and sometimes even plain wrong. Most people that I have met treat norms and standards as if they were written by a benevolent god. But if you think about it, even if the people writing those standards have perfect subject-matter knowledge (which I assume they do not) then they still have no incentive to put additional effort into fine-tuning these standards so that they provide value for applied information security. As a result, the standards are a pile of ideas and should be consulted with this consideration in mind. Industry norms are widely trusted, independent documents. Therefore, they are often misused to justify recommendations. A consultant relying heavily on industry norms is one to stay away from.
I am aware of one high-impact job in information security. According to their website, Anthropic is looking for a person to secure their assets. The picture below is an excerpt from the ad.
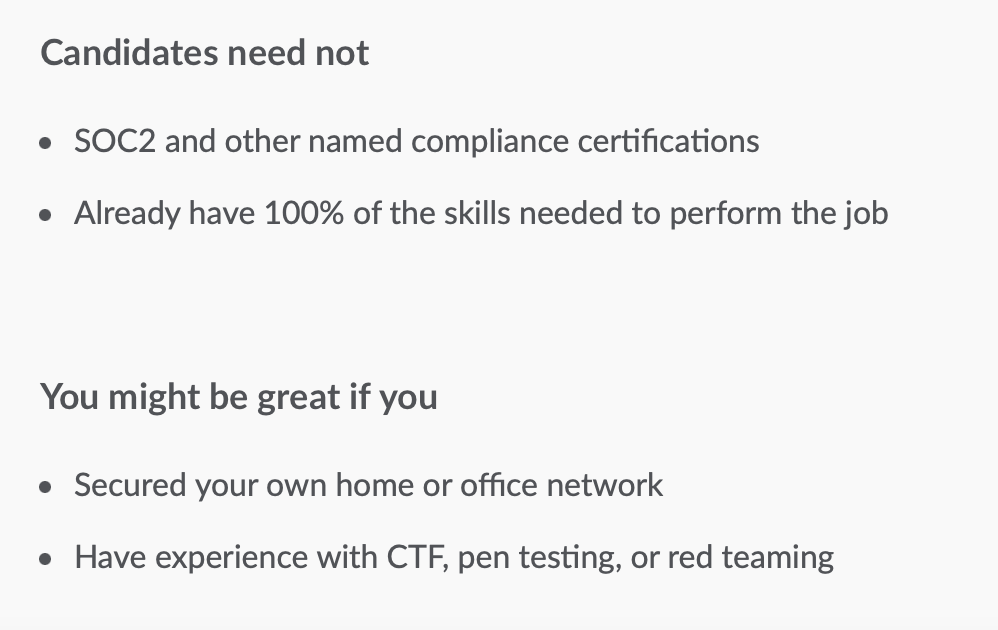
The people from Anthropic also seem to value hands-on experience over formal training. If you want to make a difference, become a hacker, not a consultant.
Biosecurity: I have witnessed and survived the use of non-mathematical metrics, poor standards and non-probabilistic security concepts. To protect myself, I have developed something like an antenna for such bullshit. When I read about biosecurity, my alert goes off. I do not know anything about biosecurity, but if the field suffers the same issues, that is a much bigger problem. Do not hesitate to contact me if this rings true to you.
If you are working in information security, consulting or both: Leave a comment and let the community know what you have experienced, especially if your experience contradicts mine!

Can you say more about why you recommend not pursuing formal certificates? Does that include even the "best" ones, e.g. from SANS? I've been recommending people go for them, because they (presumably) provide a guided way to learn lots of relevant skills, and are a useful proof of skill to prospective employers, even though of course the actual technical and analytic skills are ultimately what matter.
It is simply that the certificates that I happen to know about have poor tests that do not actually signal ability to estimate security. I do not know much about the certifications from SANS except that the training is indeed quite broad.
According to their website, the test for the GICSP certification consists of 115 questions (I assume multiple choice) of which 70% have to be correct in order to get the certification. Depending on how the answers relate to points, I guess that I could get the certification with a couple of tries and little actual knowledge.
Almost everyone of my colleagues had a G**** certification and I am not too impressed by their abilities. Therefore, I assume that it is rarely useful to pursue a certification if you can self-teach instead (or have a very good mentor/teacher at hand).
Interesting, thanks.
My background: I spent about 6 years building security products in 3 companies (from the point of view of a software developer, mainly. This is different, and in many ways "inferior" to your experience, even if it is longer). Software security is also a very common occupation in my social group (and in my ecosystem (Israel)).
My impression is that almost the entire software industry is busy helping companies put a checkbox that they "have this security feature" and adds little to actual security.
In one "company" I worked for, this wasn't the situation, it was actually very serious and actually aiming to be incredibly secure, but I prefer not talking about it publicly.
I think that someone like you would be really valuable for a company like Anthropic to get ACTUAL SECURITY rather than hiring some person with lots of credentials. If this domain attracts you (and it is only the culture that you hate), I'd like to encourage you to go ahead and do it right. Perhaps you could even build (or find and join?) a community of people trying to do actual security instead of waving around diplomas.
I have personally had too much of this nonsense and intend to never go working on security stuff again.
Thanks for your response! I am leaving InfoSec for now as well.
I've been working as a information security specialist for a year now (doing SOC work, pentests and developing tools to improve the first two) at a major energy producer in Europe. I've been a hacker and following what's going on in this field for some time longer.
I haven't done consulting but what I've heard from colleagues about some consulting companies (even internationally recognized ones) we've hired in the past matches what you've highlighted - utter disappointment.
Even though I haven't approached the field from a consulting direction, I'd also recommend instead to start hacking yourself and applying the recommendations highlighted by Hans.
I would like to push back on a couple of things - certification and norms.
There are some certificates that really take a no-bullshit stance and completing them does require extensive knowledge and abilities so seeing that someone has a OSCE certificate shows me that they are capable of doing penetration tests. I've heard other experts in the field expressing that certificates aren't that important for getting a job and what matters more is what you can do and what you are enthusiastic about doing.
Your wording on the usage of norms, I feel, is too broad. I agree that some norms, especially if they are thrown around without specifications or are implemented without background knowledge, are stupid (well explained by LiveOverFlow https://youtu.be/fKuqYQdqRIs ).
But as you said they can be good source of inspiration and ideas. For example going though the MITRE ATT&CK framework recommendations does force you to think about all the aspects a system can fail and the things highlighted there and in other standards are most often based on lessons learned from experiences where things have gone wrong.
I would also like to add to the Dos list:
Wonderful! Thank you for sharing this. What you said about norms totally makes sense. Maybe I will re-sharpen the article.
My experience as a recipient of security consultants' advice matches what you are saying. The sole result has been paperwork. Admittedly, some of this paperwork has actually been helpful (IT workers are not always very good at writing documentation.) but I still don't think it was worth the opportunity cost.
This has the ring of truth to it.
Thanks! Edited.